The October 7 anniversary has again proven to be a powerful mobilization trigger for global hacktivist networks, sparking a surge in politically motivated cyberattacks against Israeli systems.
Data from Radware reveals that between October 6 and 8, 2025, more than 50 DDoS attack claims were posted online over 14 times the daily average recorded during September.
The escalation marks a consistent pattern observed during this symbolic period since 2023, as hacktivists harness political anniversaries to amplify operations.
Surge in Symbolic and Coordinated Attacks
Hacktivist channels on Telegram and X (formerly Twitter) turned into coordination hubs for real-time attack chatter and propaganda sharing.
The campaign began when Sylhet Gang, acting as a mobilization nucleus rather than a technical operator, circulated public calls for cyber action targeting Israeli infrastructure.
Although its own DDoS claims and alleged system breaches lacked verification, Sylhet Gang’s messaging spurred multiple collectives to join the operation.
Its Telegram posts claimed compromises of servers across Israeli and European networks, with references to website defacements and data exfiltration attempts.
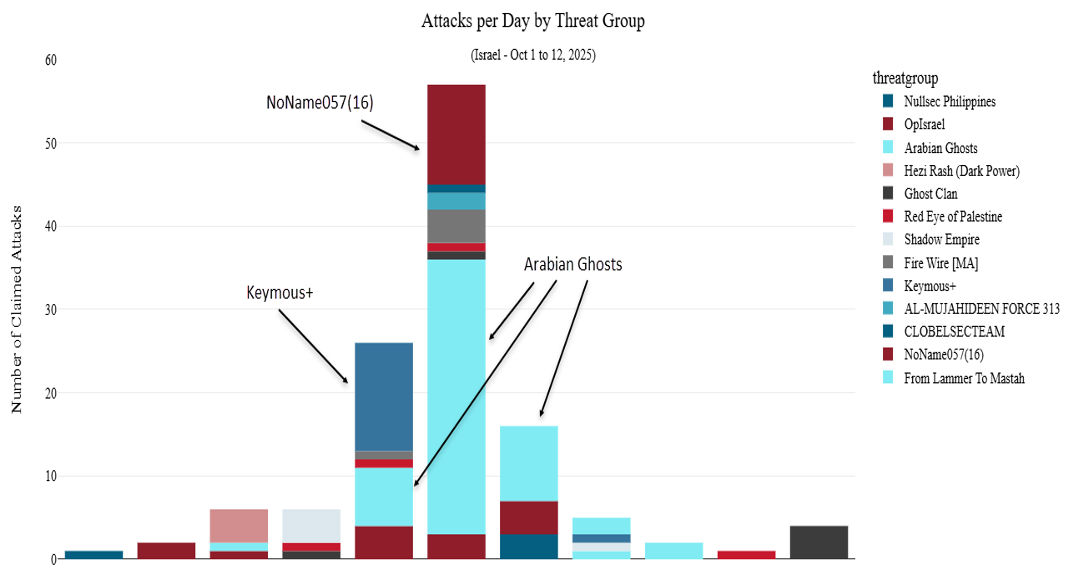
Arabian Ghosts quickly emerged as the most prolific participant, responsible for over 40% of total DDoS declarations.
Operating via its “MADGHOST” channel, the group combined propagandist amplification with direct action, publishing check-host verification links supporting its disruption claims.
Many of its attack messages included hashtags such as #OpIsrael and references to “Al-Aqsa Flood,” symbolically aligning its activities with the Palestinian resistance narrative.
Russian-Aligned Actors Expand Offensive Participation
The involvement of NoName057(16), a notorious pro-Russian hacktivist group, marked an expansion of scope and coordination across ideological divides.
Already known for anti-Western DDoS campaigns, NoName057(16) deployed its DDOSIA volunteer botnet network against Israeli government sites and even extended activity to German systems identified as pro-Israel.
Attack confirmations were accompanied by latency logs and HTTP response screenshots, signaling attempts to legitimize their operations publicly.
This cross-targeting reveals an emerging hybrid narrative where Russian-aligned collectives coalesce around common political opponents, strengthening the global hacktivist fabric.
Technical Patterns and Short-Lived Impact
Other participants, such as Keymous+, executed rapid coordinated DDoS strikes against financial and insurance entities. Posts containing traceroute logs and proof-of-disruption screenshots indicated utilization of lightweight botnets and spoofed IP floods.
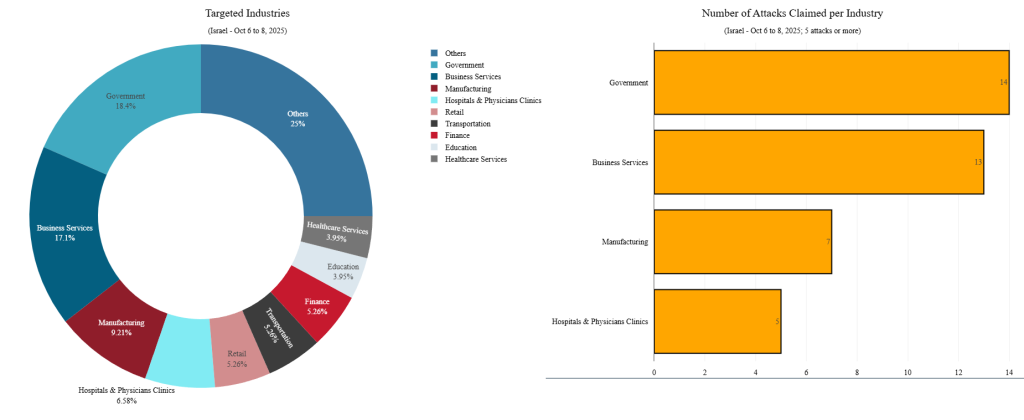
According to Radware’s telemetry, most incidents lasted less than 20 minutes, pointing to transient bursts rather than persistent penetration attempts.
Target selection skewed toward high-visibility and symbolic assets, government portals, transactional platforms, and e-commerce domains chosen for maximum psychological and media exposure rather than strategic damage.
Between October 6 and 8, claimed DDoS volumes rose nearly 200% week-over-week, reaffirming how politically charged anniversaries serve as rallying points for cyber collectives.
Ideologically diverse groups continue merging resources and narratives, transforming symbolic aggression into synchronized digital offensives.
Find this Story Interesting! Follow us on Google News , LinkedIn and X to Get More Instant Updates